Mfa Office 365 Require Selected Users to Provide Contact Methods Again
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical back up.
Users in Azure Advert have two distinct sets of contact information:
- Public profile contact information, which is managed in the user profile and visible to members of your organization. For users synced from on-premises Agile Directory, this data is managed in on-premises Windows Server Active Directory Domain Services.
- Authentication methods, which are ever kept private and simply used for authentication, including multi-factor authentication (MFA). Administrators tin can manage these methods in a user's hallmark method bract and users can manage their methods in Security Info page of MyAccount.
When managing Azure AD Multi-Cistron Authentication methods for your users, Authentication administrators can:
- Add authentication methods for a specific user, including phone numbers used for MFA.
- Reset a user's password.
- Crave a user to re-register for MFA.
- Revoke existing MFA sessions.
- Delete a user'south existing app passwords
Add hallmark methods for a user
You tin can add authentication methods for a user via the Azure portal or Microsoft Graph.
Note
For security reasons, public user contact information fields should not exist used to perform MFA. Instead, users should populate their hallmark method numbers to be used for MFA.
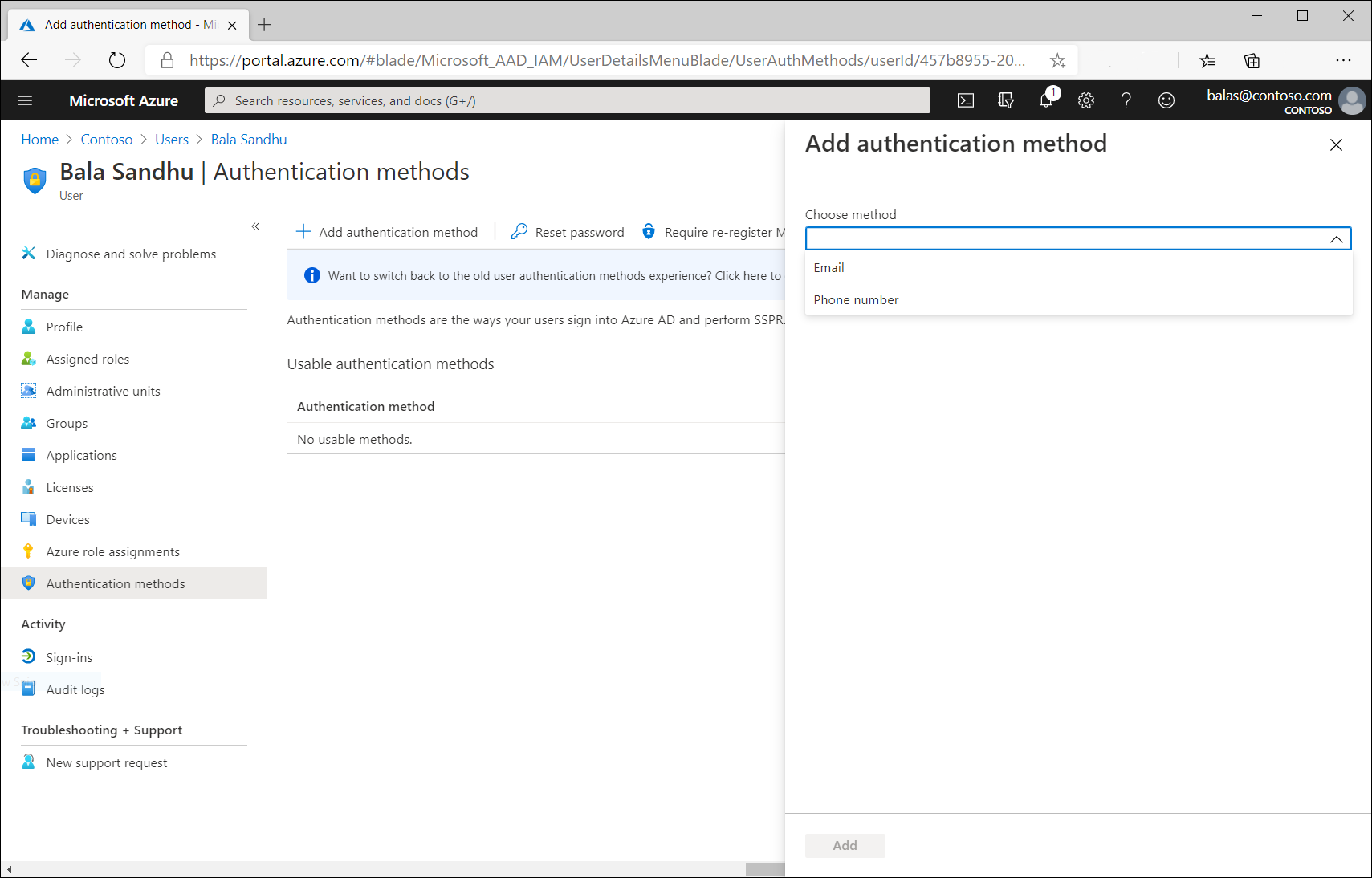
To add authentication methods for a user via the Azure portal:
- Sign into the Azure portal.
- Browse to Azure Active Directory > Users > All users.
- Choose the user for whom y'all wish to add an authentication method and select Hallmark methods.
- At the elevation of the window, select + Add hallmark method.
- Select a method (phone number or electronic mail). Email may be used for self-password reset merely not authentication. When adding a phone number, select a phone type and enter phone number with valid format (e.g. +ane 4255551234).
- Select Add.
Annotation
The preview experience allows administrators to add together any available hallmark methods for users, while the original experience only allows updating of phone and alternate phone methods.
Manage methods using PowerShell:
Install the Microsoft.Graph.Identity.Signins PowerShell module using the following commands.
Install-module Microsoft.Graph.Identity.Signins Connect-MgGraph -Scopes UserAuthenticationMethod.ReadWrite.All Select-MgProfile -Proper noun beta Listing telephone based authentication methods for a specific user.
Get-MgUserAuthenticationPhoneMethod -UserId balas@contoso.com Create a mobile phone authentication method for a specific user.
New-MgUserAuthenticationPhoneMethod -UserId balas@contoso.com -phoneType "mobile" -phoneNumber "+1 7748933135" Remove a specific telephone method for a user
Remove-MgUserAuthenticationPhoneMethod -UserId balas@contoso.com -PhoneAuthenticationMethodId 3179e48a-750b-4051-897c-87b9720928f7 Hallmark methods can also be managed using Microsoft Graph APIs, more than data can be plant in the document Azure Ad hallmark methods API overview
Manage user authentication options
If yous're assigned the Hallmark Administrator function, you can require users to reset their countersign, re-register for MFA, or revoke existing MFA sessions from their user object. To manage user settings, complete the following steps:
-
Sign in to the Azure portal.
-
On the left, select Azure Active Directory > Users > All users.
-
Choose the user yous wish to perform an activeness on and select Authentication methods. At the top of the window, then choose ane of the post-obit options for the user:
-
Reset Password resets the user's countersign and assigns a temporary countersign that must be inverse on the next sign-in.
-
Require Re-annals MFA makes it then that when the user signs in side by side fourth dimension, they're requested to set up a new MFA authentication method.
Note
The user's currently registered authentication methods aren't deleted when an admin requires re-registration for MFA. Subsequently a user re-registers for MFA, nosotros recommend they review their security info and delete any previously registered authentication methods that are no longer usable.
-
Revoke MFA Sessions clears the user's remembered MFA sessions and requires them to perform MFA the side by side fourth dimension information technology's required by the policy on the device.

-
Delete users' existing app passwords
For users that have defined app passwords, administrators can also choose to delete these passwords, causing legacy authentication to fail in those applications. These actions may be necessary if you need to provide assistance to a user, or need to reset their authentication methods. Non-browser apps that were associated with these app passwords will terminate working until a new app password is created.
To delete a user's app passwords, complete the following steps:
- Sign in to the Azure portal.
- On the left-hand side, select Azure Agile Directory > Users > All users.
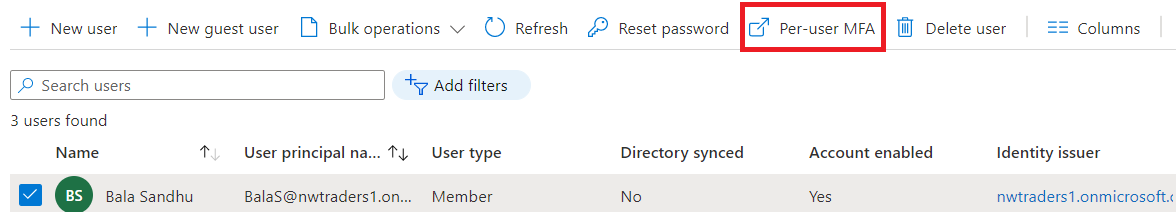
- Select Multi-Cistron Authentication. You may demand to roll to the right to encounter this menu option. Select the example screenshot beneath to see the full Azure portal window and card location:
- Check the box next to the user or users that you wish to manage. A listing of quick footstep options appears on the right.
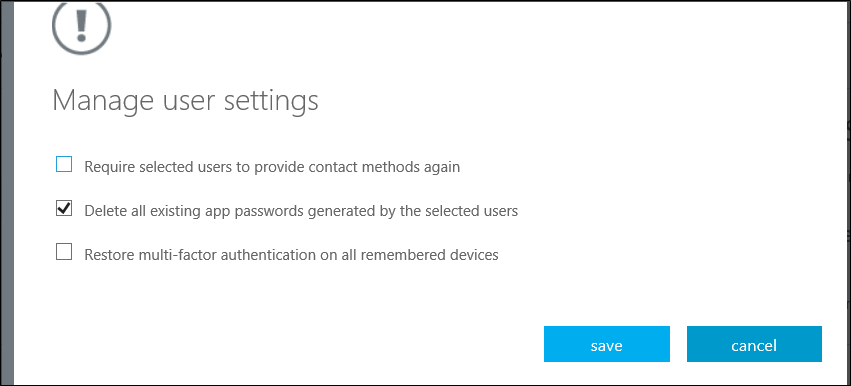
- Select Manage user settings, then cheque the box for Delete all existing app passwords generated past the selected users, as shown in the following example:
- Select relieve, then close.
Adjacent steps
This article showed you how to configure individual user settings. To configure overall Azure Advertizing Multi-Factor Authentication service settings, run across Configure Azure AD Multi-Gene Hallmark settings.
If your users demand help, see the User guide for Azure AD Multi-Factor Authentication.
Feedback
Submit and view feedback for
lakethishembled1983.blogspot.com
Source: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userdevicesettings
0 Response to "Mfa Office 365 Require Selected Users to Provide Contact Methods Again"
Postar um comentário